Rethinking Least Privilege: Zero Trust vs. Traditional Security
- Pravin Raghvani MSc
- Feb 26, 2025
- 3 min read
In today's rapidly evolving threat landscape, the principle of least privilege remains a cornerstone of effective cybersecurity. However, its implementation looks dramatically different under a Zero Trust security model compared to traditional approaches. Let's explore these differences and what they mean for your organization.

Understanding Least Privilege
At its core, least privilege means providing users, systems, and processes with only the minimum permissions necessary to perform their required functions—nothing more, nothing less. This principle helps minimize the attack surface and limit potential damage from security incidents.
The Traditional Approach: Perimeter-Based Least Privilege
In traditional security models, least privilege typically operates like this:
Trust Boundaries
The traditional model establishes clear network perimeters—inside is trusted, outside is not. Once a user authenticates at the perimeter, they often receive relatively broad access within their designated zone.
Static Access Controls
Access rights are determined primarily during initial provisioning and change infrequently. They're often role-based and tied to job titles rather than specific tasks.
Periodic Reviews
Access reviews might occur quarterly or annually, with limited ongoing verification between reviews.
Network-Centric
Security controls center around network location—internal users face fewer restrictions than external ones.
Example Scenario
An employee in finance receives all finance application permissions on day one. These permissions persist regardless of whether they're actively using each application, and access continues until manually revoked.
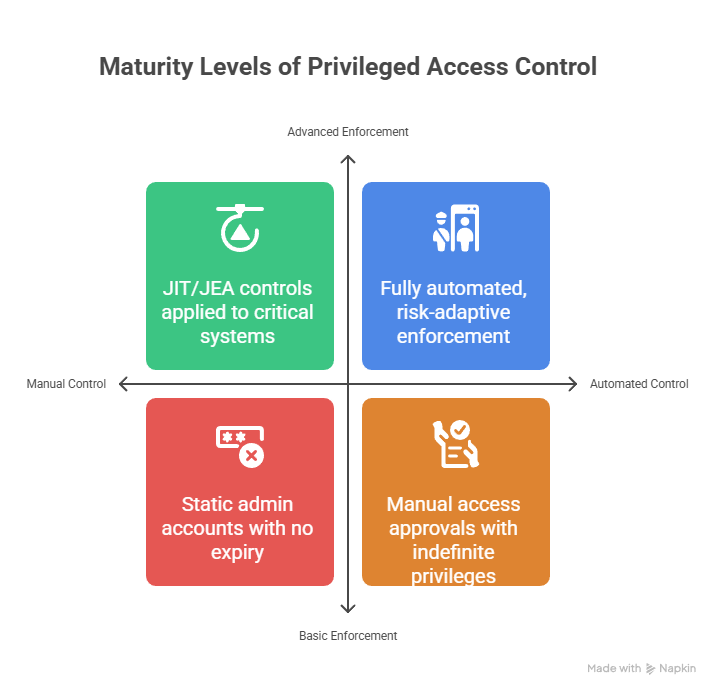
The Zero Trust Approach: Dynamic and Contextual Least Privilege
Zero Trust reimagines least privilege through a "never trust, always verify" lens:
No Default Trust
Zero Trust eliminates the concept of trusted networks, devices, or users. Every access request is treated as potentially malicious until proven otherwise.
Continuous Verification
Rather than one-time authentication, Zero Trust requires continuous assessment of trust through real-time risk analysis.
Dynamic Access Controls
Permissions are granted just-in-time, for minimum durations, and with precise scope based on current context, not just identity.
Risk-Based Evaluation
Access decisions consider multiple factors: user identity, device health, behavior patterns, resource sensitivity, and environmental risk.
Micro-Segmentation
Resources are isolated into small, well-protected segments, limiting lateral movement even after access to one resource is granted.
Example Scenario
That same finance employee needs to access payroll data. The Zero Trust system:
1. Verifies their identity with MFA
2. Confirms they're using a managed, compliant device
3. Checks that their location and timing match expected patterns
4. Grants temporary access to specific payroll functions
5. Continuously monitors behavior during the session
6. Automatically terminates access when the task is complete
Business Impact and Benefits of Zero Trust Least Privilege
Improved Security Posture
By eliminating standing privileges and requiring continuous verification, Zero Trust dramatically reduces the risk from compromised credentials and insider threats.
Enhanced Visibility
Continuous monitoring provides deeper insights into how resources are being accessed and used across your environment.
Better Compliance
Detailed access logs and precise controls simplify regulatory compliance and audit processes.
Operational Flexibility
Zero Trust models support modern work environments, including remote work, BYOD, and cloud resources, without sacrificing security.
Implementation Considerations
Transitioning to a Zero Trust model requires:
- Identity-centric security infrastructure
- Advanced authentication capabilities
- Comprehensive endpoint management
- Automated policy enforcement
- Robust monitoring and analytics
Conclusion
While traditional least privilege focuses on limiting permanent access rights within trusted boundaries, Zero Trust transforms this into a dynamic, contextual process where trust is never assumed and always verified. This shift represents not just a technical evolution but a fundamental rethinking of how we approach security in an increasingly complex digital landscape.
For organizations looking to strengthen their security posture, implementing least privilege through a Zero Trust framework offers significant advantages in reducing risk, improving compliance, and enabling the flexibility today's businesses demand.