Endpoint User Behaviour Analytics (EUBA) for Zero Trust Privileged Access Management
- Pravin Raghvani MSc
- Mar 5, 2025
- 4 min read
Updated: Jul 25, 2025
This blog post explores how Endpoint User Behavior Analytics (EUBA) can be strategically integrated with Zero Trust Privileged Access Management (ZT-PAM) to enhance security and mitigate risks associated with privileged access. We will delve into practical, real-world use cases that demonstrate how EUBA provides valuable insights into user behaviour, enabling more granular and adaptive access controls within a Zero Trust framework.

Introduction to EUBA and ZT-PAM
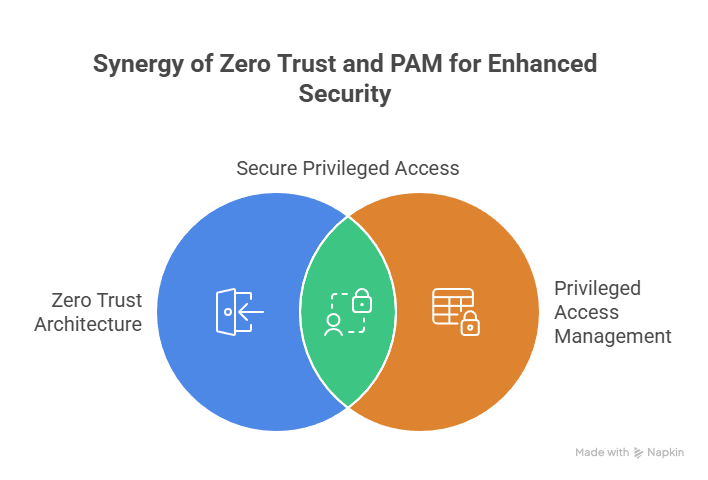
In today's complex threat landscape, traditional security models are proving inadequate. Zero Trust architecture, based on the principle of "never trust, always verify," has emerged as a robust approach to securing critical assets. Privileged Access Management (PAM) is a crucial component of Zero Trust, focusing on controlling and monitoring access to sensitive resources by privileged users. Endpoint User Behaviour Analytics (EUBA) complements ZT-PAM by providing continuous monitoring and analysis of user activity on endpoints. EUBA utilises machine learning algorithms to establish baseline behaviour patterns and identify anomalies that may indicate insider threats, compromised accounts, or policy violations.
Real-World Use Cases: EUBA-Enhanced ZT-PAM
Here are some practical use cases illustrating how EUBA can be effectively leveraged within a ZT-PAM framework:
1. Dynamic Risk Scoring and Adaptive Access Control
Problem: Static access controls in traditional PAM systems often grant excessive privileges, increasing the attack surface.
Solution: Integrate EUBA with your PAM solution to dynamically assess user risk based on their behaviour. EUBA analyses endpoint activity, such as:
Process Execution: Monitoring the execution of unusual or unauthorised processes.
File Access: Tracking access to sensitive files and folders.
Network Connections: Identifying connections to suspicious or unknown IP addresses.
Command-Line Activity: Analysing command-line usage for potentially malicious commands.
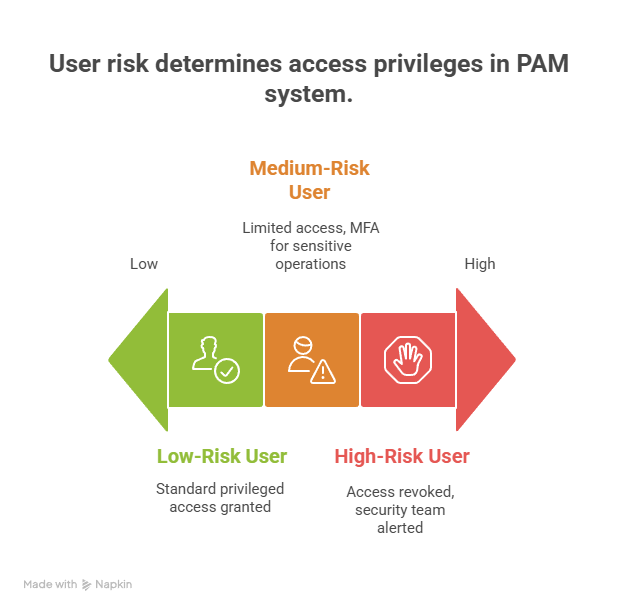
Based on this analysis, EUBA assigns a risk score to each user session. This risk score is then fed into the PAM system, which dynamically adjusts access privileges. For example:
Low-Risk User: Granted standard privileged access.
Medium-Risk User: Access is limited to specific resources or requires multi-factor authentication (MFA) for sensitive operations.
High-Risk User: Access is immediately revoked, and the security team is alerted.
Technical Terms: Risk scoring, adaptive authentication, dynamic authorisation, behavioural biometrics.
2. Anomaly Detection and Real-Time Session Monitoring
Problem: Privileged sessions can be compromised after initial authentication, allowing attackers to perform malicious activities undetected.
Solution: EUBA continuously monitors privileged sessions in real-time, looking for anomalous behaviour that deviates from established baselines. Examples include:
Unusual Command Sequences: Detecting command sequences that are rarely or never used by the user.
Lateral Movement: Identifying attempts to access resources outside the user's normal scope.
Data Exfiltration: Monitoring for large file transfers or unusual network activity that may indicate data theft.
Credential Harvesting: Detecting attempts to access or steal credentials stored on the endpoint.
When anomalous behaviour is detected, the PAM system can take immediate action, such as:
Terminating the Session: Immediately ending the privileged session to prevent further damage.
Recording the Session: Capturing a video recording of the session for forensic analysis.
Alerting Security Team: Notifying the security team to investigate the incident.

Technical Terms: Session recording, anomaly detection, behavioural analysis, threat intelligence integration.
3. Insider Threat Detection and Prevention
Problem: Malicious insiders with privileged access can be difficult to detect using traditional security measures.
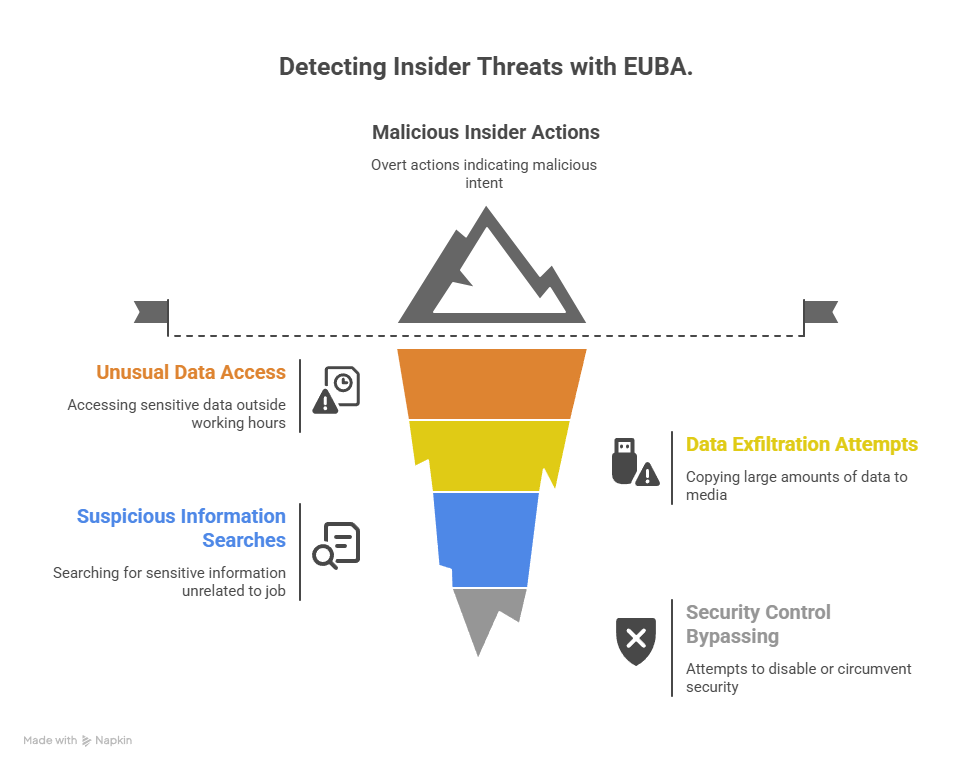
Solution: EUBA can identify insider threats by analysing user behaviour patterns and detecting deviations that may indicate malicious intent. Examples include:
Accessing Sensitive Data Outside Working Hours: Monitoring access to sensitive data during unusual times.
Copying Large Amounts of Data to Removable Media: Detecting attempts to exfiltrate data using USB drives or other removable media.
Searching for Sensitive Information: Identifying searches for sensitive information that is not related to the user's job responsibilities.
Bypassing Security Controls: Detecting attempts to disable or circumvent security controls.
By identifying these behaviours, EUBA can provide early warning of potential insider threats, allowing security teams to take proactive measures to prevent data breaches and other security incidents.
Technical Terms: User and Entity Behaviour Analytics (UEBA), data loss prevention (DLP), insider threat program, security information and event management (SIEM).
4. Just-in-Time (JIT) Access Enhancement
Problem: Even with JIT access, there's a risk of misuse during the granted timeframe.
Solution: EUBA can monitor user behaviour during the JIT access window. If anomalous behaviour is detected, the JIT access can be revoked immediately, even before the scheduled expiration. This ensures that even temporary privileged access is continuously monitored and controlled.
Technical Terms: Least privilege, ephemeral access, continuous authentication.

Conclusion
Integrating EUBA with ZT-PAM provides a powerful combination for enhancing security and mitigating risks associated with privileged access. By leveraging EUBA's ability to analyse user behaviour and detect anomalies, organisations can implement more granular and adaptive access controls, detect insider threats, and respond to security incidents in real-time. This proactive approach strengthens the Zero Trust posture and helps protect critical assets from unauthorised access and misuse.
In our Smart Access PAM Framework, this is a maturity capability within the "Monitoring and Detection" pillar.
