top of page
ACCESS GRANTED


From Firefighting to Frameworks: Why I Built Smart Access PAM
🗨️ Interview Format This article is based on a candid conversation with ChatGPT , where I shared the real story behind the Smart Access...
4 min read


Dynamic Access Controls and Zero Trust for Privileged Access: A Real-World Approach
Discover how Dynamic Access Controls aligned with Zero Trust principles transform privileged access, reduce risk, and prevent unauthorised change.
5 min read
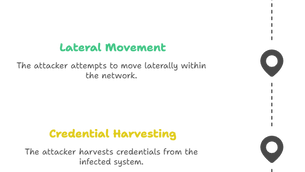
Ransomware Attack Thwarted by Zero Trust PAM: A Case Study
This document outlines a simulated ransomware attack scenario and demonstrates how a Zero Trust Privileged Access Management (PAM)...
4 min read


Zero Trust Strategy Starts with Privilege
Why Privileged Access Management is the First Step in Business-Aligned Cyber Strategy Zero Trust Isn’t Just Technical—It’s Strategic...
2 min read


Why “Castle and Moat” Security No Longer Works
Rethinking Security: Why Traditional 'Castle and Moat' Defenses Fall Short in a Zero Trust Approach For decades, organizations built...
2 min read


Mastering Zero Trust Security with Smart Access PAM Solutions
In today's ever-evolving digital landscape, cybersecurity remains a top priority for organizations looking to safeguard their sensitive...
2 min read


Endpoint User Behaviour Analytics (EUBA) for Zero Trust Privileged Access Management
This blog post explores how Endpoint User Behavior Analytics (EUBA) can be strategically integrated with Zero Trust Privileged Access...
4 min read


Modern Privileged Access Management: Evolving Approaches to Permission Models
Modern PAM strategy should include a path to Zero Standing Permissions to reduce the attack surface.
2 min read


Unraveling the Connection: How ABAC Complements the Zero Trust Strategy
In the ever-evolving landscape of cybersecurity, the Zero Trust model has gained significant traction for its proactive approach to...
2 min read


Zero Trust Strategy vs Traditional Security Strategy: A Paradigm Shift in Cybersecurity
Zero Trust Strategy and Traditional Strategy are you ready to shift to a new paradigm?
2 min read


Modern Zero Trust Architecture: Redefining Cybersecurity
In today's rapidly evolving digital landscape, traditional security models are no longer sufficient to protect organisations from...
2 min read


The Modern Zero Trust Model
Overview: Zero Trust is a cybersecurity approach that denies access by default, only granting it based on continuous, risk-based...
1 min read


Secrets to Cyber Transformation: Zero Trust Strategy Revealed
In the ever-evolving landscape of cybersecurity, staying ahead of potential threats is crucial for businesses of all sizes. One approach...
2 min read
bottom of page
