Modern Privileged Access Management: Evolving Approaches to Permission Models
- Smart Access IAM Transformation
- Mar 4, 2025
- 2 min read
Updated: May 28, 2025
Introduction
Privileged Access Management (PAM) has undergone significant transformation in recent years, with organisations increasingly moving away from traditional persistent access models to more dynamic, secure approaches like zero standing permissions.

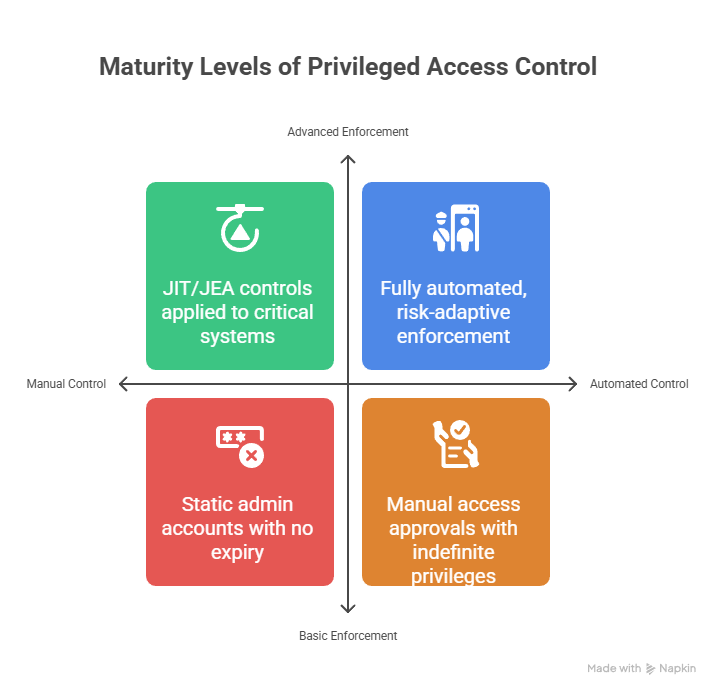
Persistent Permissions Model
Traditional Approach
Definition: Persistent permissions grant users continuous, long-term access to privileged systems and resources
Characteristics:
Standing administrative accounts with constant elevated access
Predefined access rights that remain active indefinitely
Typically used in legacy infrastructure and traditional IT environments
Drawbacks
Increased attack surface
Higher risk of credential compromise
Difficult to track and audit access
Violates the principle of least privilege (PoLP)
Complex access revocation process
Zero Standing Permissions Model
Modern Approach
Definition: Dynamic, just-in-time (JIT) access model where privileged access is granted temporarily and only when explicitly required
Key Principles:
Minimal standing privileges
Ephemeral, time-limited access
Granular, context-aware authorisation
Automated access provisioning and revocation
Benefits
Significantly reduced security risk
Improved compliance and auditability
Enhanced visibility into access patterns
Alignment with zero trust security framework
Minimised potential for unauthorised access
Implementation Strategies
Zero Standing Permissions Techniques
Just-in-Time (JIT) Access
Temporary elevation of privileges
Automatically expires after a predefined time
Requires explicit approval and justification
Temporary Credentials
Dynamically generated, short-lived credentials
Automatically rotated and invalidated
Strict time-based and context-based controls
Privileged Access Brokers
Centralised systems manage access requests
Real-time authorisation and monitoring
Comprehensive audit trails
Transition Considerations
Migration from Persistent to Zero Standing
Comprehensive identity and access management (IAM) assessment
Gradual implementation with pilot programs
Investment in automation and identity governance tools
Cultural shift towards a security-first mindset
Emerging Trends
Integration with artificial intelligence for adaptive access control
Increased use of behavioural analytics
Continuous authentication mechanisms
Deeper integration with cloud and hybrid environments
Conclusion
The shift from persistent to zero standing permissions represents a fundamental reimagining of privileged access. Organisations embracing this model can significantly enhance their security posture, reduce risk, and create more resilient, adaptable access management strategies.