top of page
ACCESS GRANTED

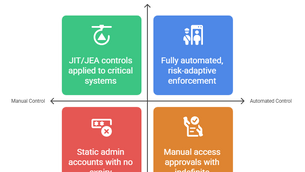
Access Control & Enforcement: Moving from Static Privilege to Dynamic, Risk-Aware PAM
Would you give every employee in your company a master key that opens every door — forever? Of course not. But in many organisations,...
3 min read

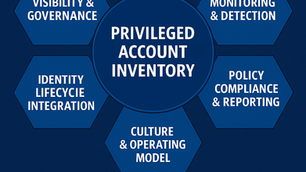
Visibility & Governance: Why Your PAM Program Lives or Dies on the Privileged Account Inventory
Analogy — You can’t defend what you can’t see Imagine running a fire safety program for a skyscraper without knowing where all the rooms...
4 min read

Another Framework? Yes, If You Want Your PAM Program to Work
Why Every Privileged Access Management Program Needs a Capability Framework to Achieve Real Maturity “Another framework? No thanks.”...
4 min read


From Firefighting to Frameworks: Why I Built Smart Access PAM
🗨️ Interview Format This article is based on a candid conversation with ChatGPT , where I shared the real story behind the Smart Access...
4 min read


Dynamic Access Controls and Zero Trust for Privileged Access: A Real-World Approach
Discover how Dynamic Access Controls aligned with Zero Trust principles transform privileged access, reduce risk, and prevent unauthorised change.
5 min read
Ransomware Attack Thwarted by Zero Trust PAM: A Case Study
This document outlines a simulated ransomware attack scenario and demonstrates how a Zero Trust Privileged Access Management (PAM)...
4 min read


The Rise of the Risk Exception: Why Vault & Manage PAM Strategies Are No Longer Enough.
Introduction: The traditional approach to Privileged Access Management (PAM), often referred to as the "Vault & Manage" strategy, has...
4 min read

From Strategy to Execution – Your PAM Action Plan
Privileged Access Management is a journey—here’s how to start well. Boards and CISOs often ask: Where do we begin? The Executive PAM...
1 min read


The PAM Investment Business Case
Good PAM is expensive. Bad PAM is unaffordable. To justify investment: · Link PAM to top cyber risks (e.g. ransomware, insider...
1 min read


PAM Metrics that Matter
What gets measured, gets managed. Executives need clear indicators that PAM is: · Reducing risk · Improving assurance...
1 min read

Non-Human Identities – The Invisible Risk
Machines have privilege, too. APIs, service accounts, and automation scripts—all hold elevated access, often with no lifecycle...
1 min read


Aligning PAM to the Regulatory Horizon
Regulators are no longer passive on identity risk. New UK and EU directives demand robust governance over digital identities, especially...
1 min read


PAM and the Human Factor
Every privileged breach has a human fingerprint. Whether it’s an overworked admin making an error or a disgruntled employee turning...
1 min read


The Case for Continuous Assurance
Audit once, expose forever. That’s the risk when PAM is treated as a tick-box annual control. Today’s threat landscape demands...
1 min read


Strategic Decision Paralysis – Where Does PAM Fit?
In a sea of competing cyber risks, why should privileged access rise to the top? Executives face daily pressure to prioritise cyber...
1 min read


The Hidden Boardroom Risk
Privileged access is not just an IT control—it's a hidden strategic liability. In boardrooms across the UK and EU, cyber risk is firmly...
2 min read


Zero Trust Strategy Starts with Privilege
Why Privileged Access Management is the First Step in Business-Aligned Cyber Strategy Zero Trust Isn’t Just Technical—It’s Strategic...
2 min read


From the PAM Trench: First Objective Define Privileged Access
To establish a strong foundation for Privileged Access Management (PAM) , organisations must start by clearly defining what privileged...
4 min read


From the Trenches: Confronting the Hidden Threat of Privileged Service Accounts
Unveiling the silent risks of unmanaged service accounts and charting a path to secure them. Introduction In the realm of cybersecurity,...
2 min read


The Clock is Ticking – Why Now is the Time to Act on Privileged Access
We’ve explored the unseen risks of privileged access, the strategic advantages of Smart Access PAM, and the need to shift from outdated...
2 min read
bottom of page
