Access Control & Enforcement: Moving from Static Privilege to Dynamic, Risk-Aware PAM
- Pravin Raghvani MSc
- Aug 11, 2025
- 3 min read
Updated: Aug 12, 2025
Would you give every employee in your company a master key that opens every door — forever? Of course not. But in many organisations, privileged access works exactly like that: over-permissioned accounts, static rights, and blanket access policies.
This “set and forget” approach is the digital equivalent of handing out a universal key after a single ID check and never questioning it again. In today’s threat landscape, that’s not just risky — it’s an open invitation to attackers.
NIST CSF Alignment: PR.AC - Access Control
The NIST Cybersecurity Framework’s Protect Function includes Access Control (PR.AC), which mandates:
Access is limited to authorised users, processes, and devices.
Privileges follow the principle of least privilege.
Access rights are reviewed and adjusted dynamically as needed.
In regulatory terms, DORA, NIS2, and the UK Cyber Resilience Act all demand demonstrable controls over administrative access, including the ability to restrict, revoke, and evidence those controls on demand.
Where Visibility Meets Action
Access Control & Enforcement is where Visibility & Governance become operational. Once you know who has privileges and where they exist, the next step is deciding when, how, and under what conditions those privileges can be used — and enforcing that consistently, adaptively, and with proof.
Why this is hard — and why it matters
Challenges:
Legacy privilege models — Standing admin rights that never expire.
Operational pressure — “Just give them admin rights to get it done” culture.
Tooling gaps — No capability for dynamic or contextual enforcement.
Cultural resistance — Pushback from admins who see adaptive controls as “slowing things down.”
Consequences of failure:
Attackers are exploiting standing privileges for lateral movement.
Non-compliance with regulatory requirements for access control.
Increased insider threat risk from excessive permissions.
Modern Enforcement Approaches
Just-in-Time (JIT) Access Privileges are granted only when needed, for a specific task, and revoked automatically after use.
Just-Enough Access (JEA) Scope is restricted to exactly the systems, commands, or files needed to complete a task.
Dynamic Access Controls Access decisions are influenced by context — such as device health, geolocation, or time of day — and automatically blocked if conditions don’t match policy.
Adaptive Access continuously re-evaluates access during the session using real-time risk signals, such as behavioural anomalies or threat intelligence feeds.
Break-Glass Access with Audit Emergency access is granted only under strict controls, with heightened monitoring and mandatory post-use review.
The Smart Access PAM Capability Framework Connection
Depends on Visibility & Governance to know exactly which accounts require control.
Strengthens Monitoring & Detection by ensuring all privileged activity is authorised and time-bound.
Enables Policy Compliance & Reporting with clear, auditable evidence of enforcement.
Supports Identity Lifecycle Integration by revoking rights immediately when roles change.
Measuring Progress: The Smart Access PAM Maturity Framework
Strategic Objective:
To what extent does the organisation enforce least privilege, context-aware, and time-bound controls for all privileged access?
What we look for:
No standing privileges unless explicitly accepted.
Dynamic and contextual enforcement capabilities are in place.
Integrated workflows for requesting, approving, and revoking access.
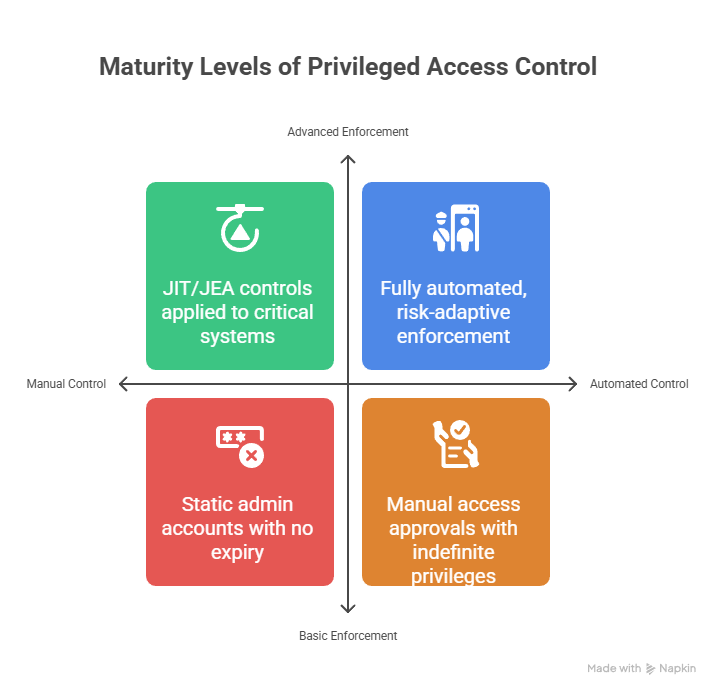
Maturity Levels:
Level 0 — Static admin accounts, no expiry, no enforcement beyond initial approval.
Level 1 — Manual access approvals; privileges often left standing indefinitely.
Level 2 — JIT/JEA controls applied to some critical systems.
Level 3 — Broad adoption of JIT/JEA; dynamic policy checks in place.
Level 4 — Fully automated, risk-adaptive enforcement integrated with PAM/IAM and threat intelligence.
The Critical Question for CISOs
If a regulator, auditor, or cyber insurer asked you to prove that:
No privileged account has standing, unmonitored admin rights, and
Every privileged access request is risk-scored and approved based on context,
… could you deliver evidence within an hour?
If the answer is no, your enforcement model is a liability.
The Bottom Line
Access Control & Enforcement is the gatekeeper of privileged access. Done right, it transforms visibility into prevention, and prevention into verifiable assurance. Done wrong, it leaves your privileged account inventory as nothing more than a list of high-value targets waiting to be exploited.
The path forward is clear:
Remove standing privileges wherever possible.
Move to a dynamic, adaptive enforcement model.
Integrate enforcement with monitoring, compliance, and lifecycle processes.
PAM. Done Right. Done to Last. 📘 Explore the Smart Access PAM Capability Framework



