Another Framework? Yes, If You Want Your PAM Program to Work
- Pravin Raghvani MSc
- Aug 5, 2025
- 4 min read
Updated: Aug 8, 2025
Why Every Privileged Access Management Program Needs a Capability Framework to Achieve Real Maturity
“Another framework? No thanks.”
That’s the reaction many CISOs and cybersecurity leaders have when faced with yet another model or matrix.
And it’s fair. Framework fatigue is real.
But when it comes to Privileged Access Management (PAM) — especially in complex, regulated, and risk-heavy environments — skipping a capability framework is the fastest way to guarantee inconsistent outcomes, rising risk exceptions, and failed maturity goals.
Let's break this down further....
🏗 The Skyscraper Without Blueprints
A PAM strategy without a capability framework is like trying to build a skyscraper without architectural plans.
You might start fast, throwing steel and concrete together. But without a blueprint:
Floors don’t align
Load-bearing walls are missing
Wiring and plumbing don’t connect
Safety inspections become nightmares
It might look complete, but it won’t survive the first storm.
The Smart Access PAM Capability Framework is that blueprint:
It defines the structure before you start
Guides every stage, from strong foundations (visibility) to the top floor (operating model)
Ensures the build meets safety, compliance, and performance standards

❌ When PAM Starts with Tools, Not Strategy
Many organisations treat PAM as a technology project — vault some credentials, monitor some sessions, issue a policy, and hope for the best.
This approach typically leads to:
Fragmented controls across systems and teams
Unclear ownership and accountability
Rising risk exceptions that erode Zero Trust goals
Stalled maturity because progress isn’t measured or benchmarked
And most critically… no one really knows what “good” looks like.
Without a structured strategy aligned to business risk, PAM becomes reactive, audit-driven, and ultimately unsustainable.

🧭 Why You Need a PAM Capability Framework
The Smart Access PAM Capability Framework is designed to fix this.
It’s not another checkbox exercise — it’s a business-aligned, modular structure that guides CISOs and cyber leaders through building sustainable PAM maturity across people, process, and technology.
It helps answer questions like:
Are we enforcing least privilege across all access paths?
How do we prioritise PAM improvements based on business risk?
What’s our current capability vs. where do we need to be?
How do we build resilience against insider threats and ransomware?
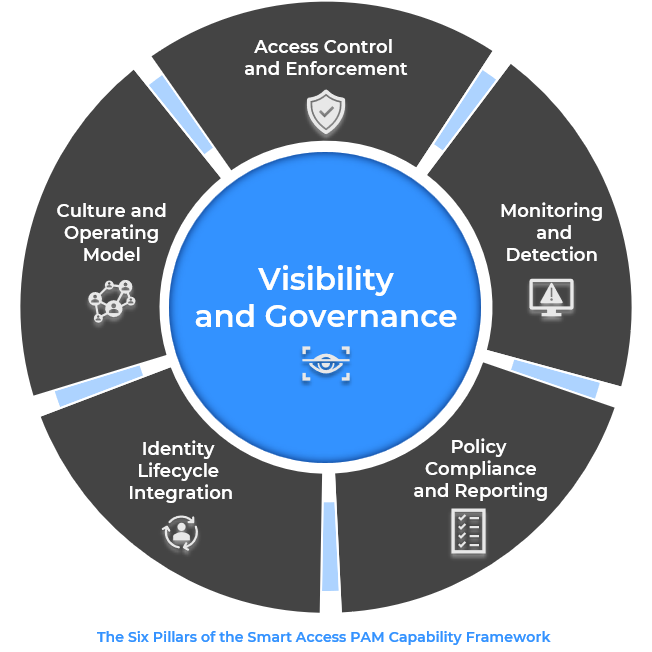
🔐 The Six Capability Pillars of Smart Access PAM
The framework is structured into six core pillars, aligned to NIST CSF 2.0 and focused on business and cyber outcomes:
1. Visibility & Governance (Core) - Map all privileged access, accounts, assets, and ownership across the environment. Visibility is the foundation of control.
2. Access Control & Enforcement - Implement least privilege by design, not exception. Enforce controls across identities, sessions, and endpoints.
3. Monitoring & Detection - Move from logging to real-time insight. Monitor for anomalous or high-risk privileged behaviour with actionable alerts.
4. Policy Compliance & Reporting - Automate control validation and policy adherence. Simplify audit readiness through continuous compliance reporting.
5. Identity Lifecycle Integration - Tie privileged access directly to joiner-mover-leaver processes to reduce exposure and improve provisioning hygiene.
6. Culture & Operating Model - Establish ownership, accountability, and user engagement. Embed PAM as a business-enabling capability, not a blocker.
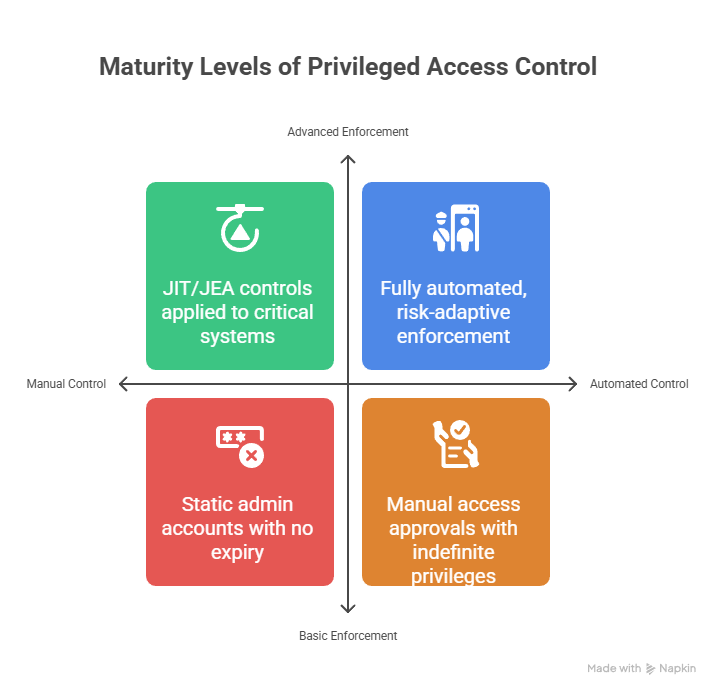
🆚 With vs. Without a Capability Framework
Let’s make this real.
Here’s how Privileged Access typically plays out without a capability framework vs. a business that adopts the Smart Access PAM Capability Framework:
Without a Framework | With the Smart Access PAM Capability Framework |
|---|---|
Tool-led deployments with no strategic roadmap | Risk-based prioritisation with business-aligned planning |
Inconsistent controls across applications, systems, and teams | Standardised capability model across the enterprise |
Risk exceptions become the norm | Risk exceptions are minimised, monitored, and governed |
Privileged access not linked to the user lifecycle | Integrated with joiner-mover-leaver workflows |
Scrambling during audits with inconsistent reporting | Streamlined, real-time compliance and reporting |
No clear ownership or cross-team coordination | Embedded roles, accountability, and operational clarity |
Maturity is assumed, not measured | Maturity is benchmarked, tracked, and improved over time |
In short:
A business without a framework is flying blind.
A business with the Smart Access PAM Capability Framework is structured, risk-aware, and progressing toward Zero Trust.
🎯Measurable Maturity, Not Just Models
Unlike traditional frameworks that exist only on PowerPoint, the Smart Access PAM Capability
Framework is:
✅ Actionable – Built for real-world teams, not just theory
✅ Risk-aligned – Prioritises based on impact and exposure
✅ Modular – Adaptable to your existing tech and org structure
✅ Measurable – Enables tracking of PAM maturity over time
✅ Zero Trust-ready – Supports dynamic control, not static perimeters
The Bottom Line for CISOs
A Privileged Access Management capability framework isn’t about bureaucracy — it’s about clarity, consistency, and control.
If your PAM program is struggling with:
Audit noise
Risk exceptions
Low adoption
Poor integration
Or stalled maturity…
You don’t need more tools. You need a blueprint.
Explore the Framework
The Smart Access PAM Capability Framework is now available as part of our blog series.
👉 Read now to learn how to assess, build, and mature each of the six capabilities in your organisation.