top of page
ACCESS GRANTED

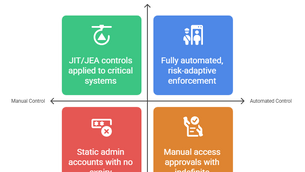
Access Control & Enforcement: Moving from Static Privilege to Dynamic, Risk-Aware PAM
Would you give every employee in your company a master key that opens every door — forever? Of course not. But in many organisations,...
3 min read


Another Framework? Yes, If You Want Your PAM Program to Work
Why Every Privileged Access Management Program Needs a Capability Framework to Achieve Real Maturity “Another framework? No thanks.”...
4 min read


From Firefighting to Frameworks: Why I Built Smart Access PAM
🗨️ Interview Format This article is based on a candid conversation with ChatGPT , where I shared the real story behind the Smart Access...
4 min read


From Strategy to Execution – Your PAM Action Plan
Privileged Access Management is a journey—here’s how to start well. Boards and CISOs often ask: Where do we begin? The Executive PAM...
1 min read


The PAM Investment Business Case
Good PAM is expensive. Bad PAM is unaffordable. To justify investment: · Link PAM to top cyber risks (e.g. ransomware, insider...
1 min read


The Clock is Ticking – Why Now is the Time to Act on Privileged Access
We’ve explored the unseen risks of privileged access, the strategic advantages of Smart Access PAM, and the need to shift from outdated...
2 min read


Why “Castle and Moat” Security No Longer Works
Rethinking Security: Why Traditional 'Castle and Moat' Defenses Fall Short in a Zero Trust Approach For decades, organizations built...
2 min read


Smart Access PAM – Building a Secure Foundation for Business Confidence
In our first post, we explored how privileged access is a hidden but critical business risk—one that’s growing in both scale and impact....
2 min read


The Hidden Business Risk in Your Digital Core
In today’s digital economy, every business is a technology business. Whether you’re delivering financial services, manufacturing...
2 min read


Stay Ahead in Cyber Security with Smart Access PAM Strategies
In today's digital landscape, the importance of cyber security cannot be overstated. With the increasing sophistication of cyber threats,...
2 min read


Unlocking Privileged Access Management Secrets for Cyber Security Leaders
In the realm of cybersecurity, one of the most critical aspects that leaders need to focus on is Privileged Access Management (PAM)....
2 min read


Zero Trust Insider Risk: Safeguarding Your Organization from Within
According to various reports, insider incidents account for approximately 20-30% of all security breaches. The frequency has been increasing
3 min read
bottom of page
