Smart Access PAM Blueprint
Built on NIST 2.0. Designed for Modern PAM
The Smart Access PAM blueprint and frameworks translate's the global NIST Cybersecurity Framework (CSF) 2.0 into a practical, business-aligned Privileged Access Management strategy — helping CISOs, CIOs, and risk leaders move from complexity to measurable control.

Why Alignment Matters
PAM is Central to Risk and Regulation
Privileged access failures are at the heart of modern cyber breaches. Regulators now expect organisations to evidence risk-based controls, not just technology.
-
NIST CSF 2.0 is the global benchmark for cybersecurity maturity.
-
Privileged Access Management (PAM) is a critical control area for compliance with NIS2, DORA, and UK Cyber Resilience frameworks.
-
Aligning PAM with NIST ensures audit readiness, cyber insurance resilience, and Zero Trust transformation.
Smart Access PAM is the only PAM blueprint built from the ground up to map directly to NIST CSF 2.0.
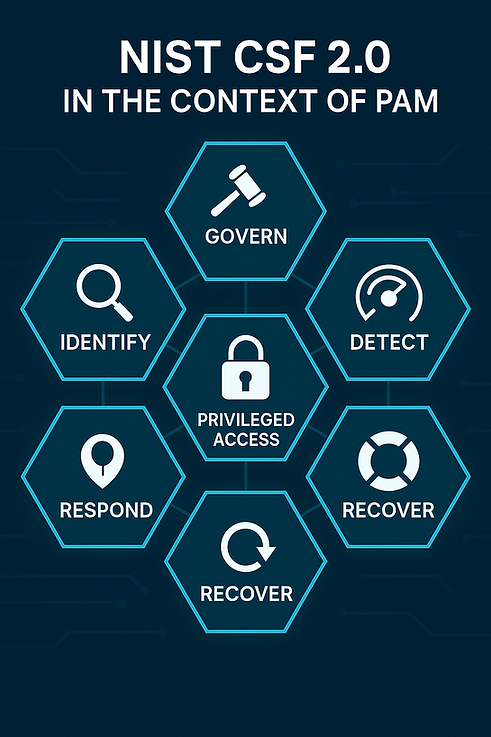
NIST CSF 2.0 in the Context of PAM
The Six Functions and Where PAM Fits
NIST CSF 2.0 defines six core functions that structure how organisations manage cybersecurity risk. Each has direct relevance to Privileged Access Management:
-
Govern (GV): Establish governance, policies, and risk oversight.
-
PAM Strategy Alignment: Define who should have privileged access, under what conditions, and how risk exceptions are managed.
-
-
Identify (ID): Understand assets, risks, and dependencies.
-
PAM Strategy Alignment: Discover privileged accounts across infrastructure, applications, and third parties.
-
-
Protect (PR): Safeguard identities, access, and data.
-
PAM Strategy Alignment: Enforce least privilege, just-in-time access, and MFA for administrators.
-
-
Detect (DE): Monitor for anomalies and threats.
-
PAM Strategy Alignment: Spot unusual privileged activity, lateral movement, or credential misuse.
-
-
Respond (RS): Contain and mitigate incidents.
-
PAM Strategy Alignment: Revoke compromised credentials, cut off malicious sessions, and coordinate response.
-
-
Recover (RC): Restore operations and resilience.
-
PAM Strategy Alignment: Reinstate secure privileged access and communicate recovery status after an incident.
-
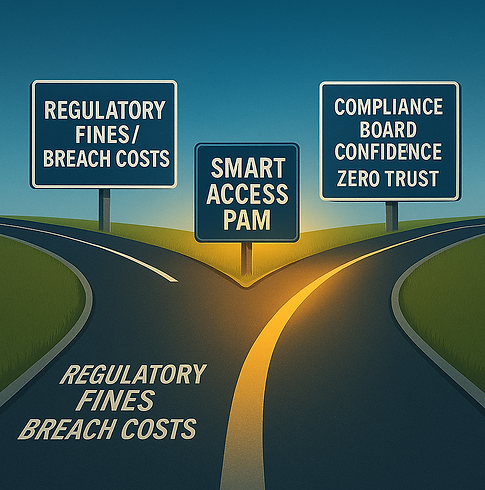
The Business Value of Alignment
Compliance, Confidence, and Resilience
Aligning PAM with NIST CSF 2.0 delivers:
-
Regulatory compliance with NIS2, DORA, UK Cyber Resilience.
-
Board-level confidence through risk-based reporting.
-
Audit success with measurable maturity indicators.
-
Reduced dwell time for advanced threats.
-
Alignment to Zero Trust strategies without vendor lock-in.
Smart Access PAM makes these outcomes practical, measurable, and sustainable.
Take the Next Step
From Awareness to Measurable Action
Take the next step:
-
Download the Smart Access PAM Blueprint (free).
-
Book a free 30-minute discovery call to discuss how the Smart Access PAM Blueprint — built on NIST CSF 2.0 — can be applied to your organisation’s PAM strategy.
