top of page
ACCESS GRANTED

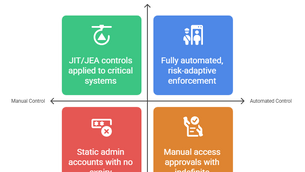
Access Control & Enforcement: Moving from Static Privilege to Dynamic, Risk-Aware PAM
Would you give every employee in your company a master key that opens every door — forever? Of course not. But in many organisations,...
3 min read

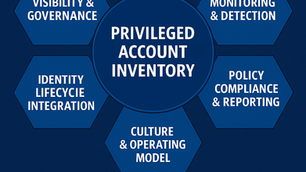
Visibility & Governance: Why Your PAM Program Lives or Dies on the Privileged Account Inventory
Analogy — You can’t defend what you can’t see Imagine running a fire safety program for a skyscraper without knowing where all the rooms...
4 min read

Another Framework? Yes, If You Want Your PAM Program to Work
Why Every Privileged Access Management Program Needs a Capability Framework to Achieve Real Maturity “Another framework? No thanks.”...
4 min read


From Firefighting to Frameworks: Why I Built Smart Access PAM
🗨️ Interview Format This article is based on a candid conversation with ChatGPT , where I shared the real story behind the Smart Access...
4 min read


The Business Value of a Structured PAM Strategy Aligned with NIST CSF
By now, we’ve uncovered a powerful truth: privileged access is one of the most critical risks in your business—and one of the most...
2 min read


The Smart Access PAM Framework: A Modern Blueprint for Privileged Access Success
To build a resilient, future-ready Privileged Access Management (PAM) capability, organisations need more than tools and quick wins—they...
2 min read
bottom of page
