The Smart Access PAM Framework: A Modern Blueprint for Privileged Access Success
- Pravin Raghvani MSc
- May 19, 2025
- 2 min read
Updated: Aug 14, 2025
To build a resilient, future-ready Privileged Access Management (PAM) capability, organisations need more than tools and quick wins—they need a blueprint. A fortress cannot be constructed from random stones; it requires engineering, a solid foundation, and a plan tailored to the terrain. The same holds true for securing privileged access. Enter the Smart Access PAM Framework—a modular, maturity-driven approach built to help organisations move from foundational gaps to advanced, Zero Trust-aligned control without hindering productivity or overwhelming internal teams.
This framework is designed for strategic leaders—CIOs, CISOs, Heads of IAM and PAM—who need a clear, scalable model for implementing PAM that supports risk reduction, regulatory alignment, and long-term business enablement.
Why a Framework Matters
Too often, PAM is approached as a point solution—a vault, a password manager, or a least-privilege policy deployed in isolation. But PAM is not a single tool. It is a system of governance, visibility, control, and culture. Without a coherent framework, even the most expensive technologies falter under the weight of complexity, stakeholder resistance, or unmanaged exceptions.
The Smart Access PAM Framework addresses this by:
Aligning with industry standards – Built on the NIST Cybersecurity Framework (CSF), the blueprint offers credibility, traceability, and consistency.
Supporting tailored implementation – Modular design allows organisations to prioritise based on specific risks, resources, and regulatory pressure.
Driving measurable maturity – Using a five-level maturity model, it helps leaders assess where they are, where they want to go, and how to get there.
Focusing on visibility first – Grounding all efforts in the discovery and governance of privileged access, because what you can’t see, you can’t secure.
The Smart Access PAM Framework: At a Glance

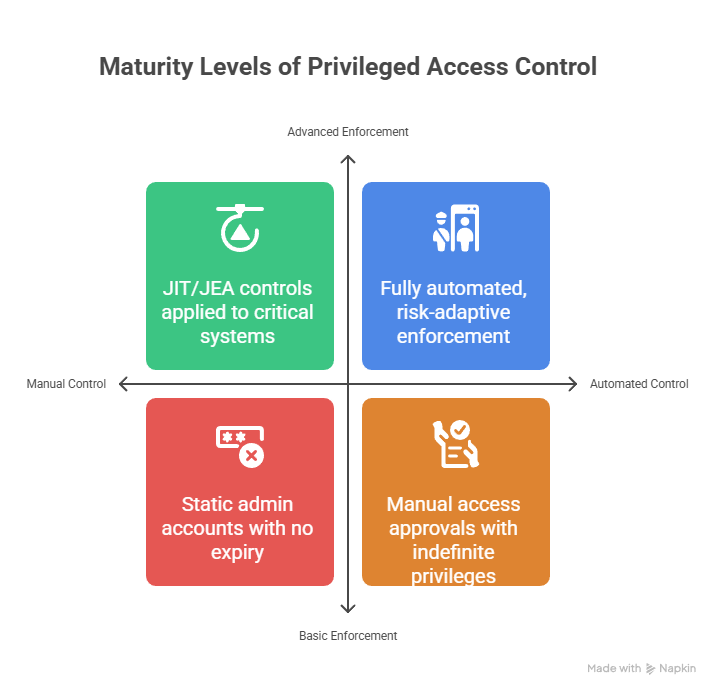
Maturity Model: A Path from Ad Hoc to Zero Trust
Each capability pillar in the framework is assessed across five levels:

Learn More About the Framework
The framework is the culmination of many years of transforming Privileged Access Management in highly regulated organisations. The six pillars are only the foundation; the framework is much broader. Learn more and get the eBook, which provides a practical guide to the framework.