top of page
ACCESS GRANTED

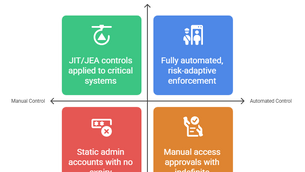
Access Control & Enforcement: Moving from Static Privilege to Dynamic, Risk-Aware PAM
Would you give every employee in your company a master key that opens every door — forever? Of course not. But in many organisations,...
3 min read


Dynamic Access Controls and Zero Trust for Privileged Access: A Real-World Approach
Discover how Dynamic Access Controls aligned with Zero Trust principles transform privileged access, reduce risk, and prevent unauthorised change.
5 min read


PAM Solutions: Capabilities for a robust PAM strategy
Introduction Privileged Access Management (PAM) solutions are vital for a strong PAM strategy, providing necessary controls, audit...
3 min read


ABAC Attributes in Zero Trust Identity Strategy
Attributed Based Access Control for Fine Grained Access Management The key to a successful ABAC implementation in a Zero Trust strategy...
2 min read


Modern Privileged Access Management: Evolving Approaches to Permission Models
Modern PAM strategy should include a path to Zero Standing Permissions to reduce the attack surface.
2 min read


Rethinking Least Privilege: Zero Trust vs. Traditional Security
In today's rapidly evolving threat landscape, the principle of least privilege remains a cornerstone of effective cybersecurity. However,...
3 min read
bottom of page
