PAM Solutions: Capabilities for a robust PAM strategy
- Pravin Raghvani MSc
- May 20, 2025
- 3 min read
Updated: May 29, 2025
Introduction
Privileged Access Management (PAM) solutions are vital for a strong PAM strategy, providing necessary controls, audit information, and secure credential management. In the past, there were only a few market leaders in this space, but recent Zero Trust strategies have introduced many new players. This expansion allows organisations to find solutions that fit their specific needs and budgets. In this blog series, I will highlight key capabilities to consider when evaluating products during a Request for Proposal (RFP) process.
What is a capability?
I prefer to use the term "capability" instead of "feature" or "technology" because it emphasises business outcomes and abilities. For instance, does this solution have the capability to identify my privileged access to an inventory, both on-premises and in the cloud?
Privileged Access Management Solution Key Capabilities
The "Key" capabilities are aligned to the pillars of the "Smart Access PAM Framework".
Core - Visibility and Governance
Privileged Access Inventory (Foundational Priority – Start Here)
Goal: Achieve full visibility into privileged accounts, identities, entitlements, and access paths.
Key Capabilities:
Continuous discovery of privileged accounts (human and machine) across on-prem, cloud, hybrid, and SaaS
Identification of standing privileges and orphaned accounts
Continuous inventory of shared accounts, service accounts, application credentials, and secrets
Mapping of privileged entitlements to roles, assets, and users
Integration with Identity Governance (IGA) and CMDB for context enrichment
Reporting and audit trails of discovered assets and privileged access paths
Business Value: Enables governance, reduces unknown risk exposure, and informs the least privilege strategy
PAM Access Management & Enforcement (Strategic Execution – Build in Layers)
Goal: Control and govern who can access what, when, how, and under what conditions.
Access Control and Enforcement

In the Smart Access PAM framework, we emphasise the need for continuous improvement. Your solution strategy should (a) securely manage credentials, (b) provide time-based access with authorisation, (c) enforce least privilege, and (d) allow dynamic access based on policies. These can be delivered through a single enterprise solution or a combination of solutions.
While strong controls are vital for securing privileged access, it's essential to account for end-user experience to prevent resistance and attempts to bypass controls.
Tier 1: Baseline Controls – Secure & Govern Access
Vaulting of shared/admin credentials with role-based access
Password rotation and check-in/check-out workflows
MFA enforcement for access to the vault and privileged sessions
Session logging and immutable audit trail generation
Role-based access control (RBAC) with segregation of duties (SoD)
🟪 Priority: Immediate deployment to control known privilege pathways
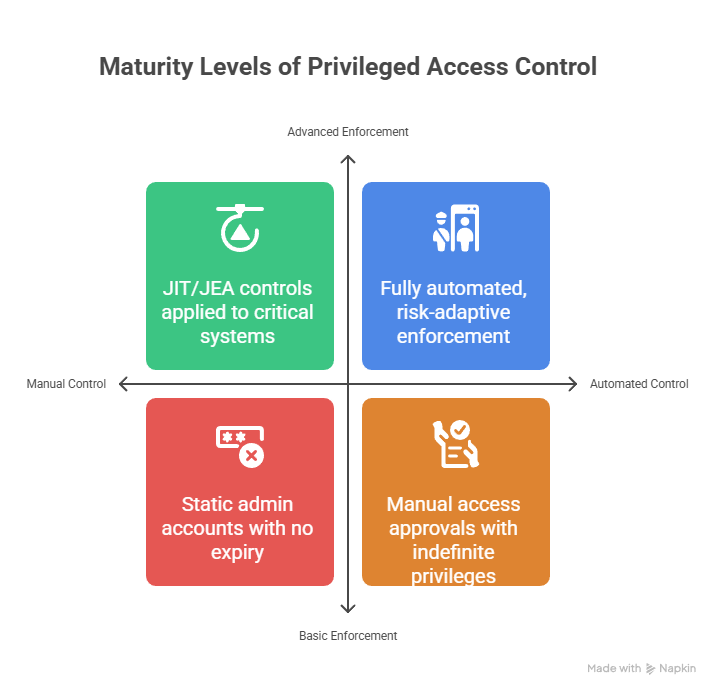
Tier 2: Just-in-Time (JIT) & Least Privilege Enforcement
Ephemeral access elevation with time-bound entitlements
Approval workflows for privileged tasks
Dynamic assignment of admin roles (e.g., Azure PIM, sudo)
Privileged access brokering without credential disclosure
Temporary assignment of local accounts or AD group membership
🟪 Priority: Drives risk reduction and audit defensibility through privilege minimisation
Tier 3: Just Enough Access (JEA) & Task-Based Controls
Task-specific privilege grants based on job functions
Command control and restriction (e.g., whitelist/blacklist commands)
Session isolation with contextual restrictions (e.g., no file transfer)
Enforcement of "break glass" access only under defined conditions
🟪 Priority: Supports granular control in sensitive or regulated environments
Tier 4: Dynamic Access & Policy-Based Access Controls (PBAC)
Attribute- and policy-based access controls (ABAC/PBAC)
Real-time risk scoring and adaptive enforcement
Contextual access (location, device posture, time, behaviour)
Continuous evaluation of trust and revocation (Zero Trust-aligned)
Integration with SIEM/SOAR for response-driven access control
🟪 Priority: Optimal state for Zero Trust, high automation, and intelligent privilege enforcement
🔷 Supporting Governance & Operating Capabilities
Privileged Access Governance
Policy definition and lifecycle management for privileged access
Access reviews and certification campaigns
SoD conflict detection and resolution
Reporting to support internal/external audits and compliance
Alignment with identity lifecycle and joiner/mover/leaver processes
Analytics & Metrics
PAM maturity scoring (e.g., % of JIT accounts vs. standing)
Risk-based dashboards (privilege creep, high-risk users)
Key Risk Indicators (KRIs) for excessive or abnormal usage
Operational metrics (access request volumes, approval times)
Integration & Ecosystem Support
IGA, SIEM, ITSM, CI/CD pipelines, cloud providers, endpoint agents
REST APIs, syslog export, identity federation, and secrets management tools
Support for hybrid infrastructure (legacy systems, cloud-native apps)
🚦Implementation Guidance by Priority
Phase | Capability Focus | Outcome |
|---|---|---|
1 | Inventory + Vaulting + MFA | Visibility + baseline control |
2 | JIT + Session Monitoring | Reduced risk + enhanced governance |
3 | JEA + Access Workflows | Granular control + task integrity |
4 | PBAC + Dynamic Policy Engine | Zero Trust maturity + agility |